VPN has various advantages, from scrambling and shielding your activity from listening in to unblocking territorial blocked sites. It can be a test to pick the correct VPN convention to use in your in-house VPN arrangement, or from a VPN supplier you pick. The principle VPN conventions being used are Protocols each VPN Protocol are like PPTP-SSTP-L2TP/IPSec-OpenVPN and some different varieties. The amount of encryption do you require however ? What’s more, what is the contrast between these encryption conventions ?
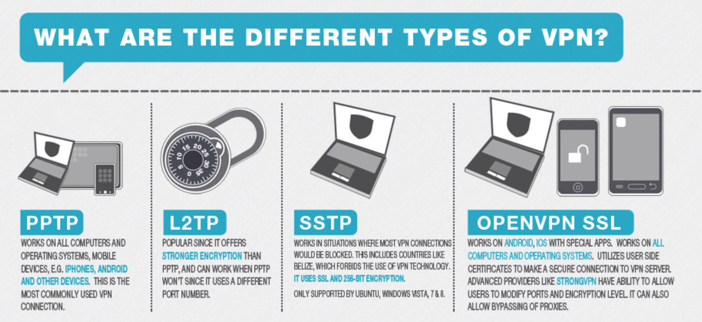
VPN PROTOCOL INFO : PPTP
PPTP VPN PROTOCOL stand for Point to Point Tunneling Protocol.
PPTP VPN PROTOCOL
Advantages
- Simple to setup.
- For all intents and purposes bolstered on each gadget with VPN support.
- Low overhead and in this way great rates.
PPTP VPN PROTOCOL Disadvantages
- Low encryption at 128 bit.
- A ton of imperfections where found in the MS PPTP VPN PROTOCOL usage. In the event that you are searching for security and protection , run now.
- Generally unsteady. On the off chance that you have utilized PPTP VPN PROTOCOL some time recently, you may realize that occasionally it takes more than once to unite. Also, associations may drop arbitrarily.
- Generally simple to hinder by ISPs.
- NSA unscrambles PPTP VPN PROTOCOL encoded activity effortlessly. No curve balls here, given most recent security instruments and cloud handling powers, any security master worth his cash presumably could without a lot of sweat.
VPN PROTOCOL : L2TP/IPSEC
L2TP VPN PROTOCOL or Layer 2 Tunneling Protocol does not do any encryption without anyone else’s input. It essentially provides the directing passage. VPN suppliers by and large utilize IPsec for encryption.
L2TP/IPSec VPN PROTOCOL Advantages
- Bolstered on most current gadgets and OSes.
- Encryption at 256bit.
- Simple to setup on MAC and Windows as it is locally upheld.
- No known significant vulnerabilities.
L2TP/IPSec VPN PROTOCOL Disadvantages
- Higher encryption implies more CPU, yet all in all that is not a biggie for present day gadgets
- Most difficult to arrange on a Linux server.
- Higher encryption with twofold embodiment results in B/W hit. What amount relies on upon your gadget and the VPN Server/Provider.
- Generally simple to obstruct by ISP.
VPN PROTOCOL : OPENVPN
OpenVPN VPN PROTOCOL is an open source application with a custom encryption convention in light of SSL/TLS key trades.
OpenVPN VPN PROTOCOL Advantages
- Bolsters equipment increasing speed with enhances speeds.
- Can cross through firewalls and NAT with extraordinary achievement. You can setup OpenVPN VPN PROTOCOL on port 443 TCP, this will make it look like HTTPS movement and difficult to identify.
- Extremely steady and dependably.
- Makes utilization of the OpenSSL libraries for encryption. The point here is that you are running an open source application with open source kept up encryption libraries. At the end of the day, the overall population is keeping up the usage and settling bugs as they show up. There are no shady government organizations or suspicious outline blemishes.
OpenVPN Disadvantages
- Restricted gadget support. If I’m not mistaken there were just a modest bunch of working OpenVPN VPN PROTOCOL applications for non-established Android and half of those did not take a shot at all Android gadgets.
- In the event that you utilize the default 128-bit blowfish you will get an incorrect conviction that all is well with the world. So in the event that you are setting up your own particular OpenVPN server change to a higher encryption convention. In the event that you do use OpenVPN at your VPN supplier ensure they don’t utilize 128-bit blowfish.
VPN PROTOCOL : SSTP
SSTP a.k.a Secure Socket Tunneling Protocol utilizes TLS 3.0 over TCP port 443 “HTTPS” at the season of composing. This makes it secure and difficult to piece.
SSTP Advantages
- High Encryption.
- Hard to recognize and piece. It utilizes the HTTPS port 443/TCP this makes it simple for SSTP to cross through firewalls and NAT.
- Upheld on all Microsoft since Vista SP1.
SSTP Disadvantages
- Not upheld by all VPN Providers.
- A Microsoft restrictive convention, not accessible for open review. Microsoft is known for it’s security issues and participation with different government organizations.
- Restricted backing for non-MS gadgets.
VPN PROTOCOL ADD-ONS :DOUBLE ENCRYPTION AND TOR
Double Encryption: Some VPN Providers have begun giving Double Encryption. Where the movement is encoded between your PC and a VPN server, then the VPN server re-scrambles the activity a second time over a connection to a second VPN server. From that point on your movement leaves to the Internet destination. This surely improves obscurity, yet I am a bit in uncertainty about the advantages of twofold encryption regarding quality of information security.
TOR : Tor is one more additional items which can be considered with and without VPN. TOR is an online free programming that is composed and assembled to battle oversight and ensure obscurity. It works by adding all the TOR clients to a worldwide system and after that movement bobs between these hubs before coming to it’s destination. Consequently making it near difficult to log and track the starting point of your movement. Given that your activity ricochets through different hubs of different clients frameworks and servers “yet scrambled” it makes TOR moderate. On the off chance that you are suspicious however, you could join VPN with TOR. See a delineation beneath on how TOR Works.
VPN PROTOCOL : ADDITIONAL CONSIDERATIONS
Logs : Some VPN suppliers do keep logs, others don’t. On the off chance that you pick a US VPN supplier it doesn’t make a difference the amount of encryption you get, according to the PATRIOT demonstration the VPN suppliers need to hand over all the information on solicitation. In the event that you pick a VPN supplier in the EU you are marginally better of. Things are way more entangle to get to your information. The EU puts more accentuation on individual security than the US government. In the event that you are jumpy you can go for a VPN supplier in Panama with no VPN activity logs, no installment logs and no legitimate email location required, a case of such a supplier is Proxy.sh.
Profound Inspection : is a propelled type of example discovery by and large connected to the information area of the parcels. This is utilized by ISPs and Governments for information mining, control, listening stealthily and different employments. On the off chance that you utilize a solid encryption convention, your protection is not in question here. Be that as it may, you have to get associated with VPN first. Profound Inspection can be utilized to follow VPN association endeavors patters and square those associations from being built up. Subsequently you wont have the capacity to get a VPN association with begin with. OpenVPN is for the most part extremely impervious to Deep investigation given that it can run both UDP/TCP on any given port utilizing an extensive variety of encryption instruments. For amusement only, a percentage of the better known nations applying Deep Packet Inspection are :
China
Russia
United States
Iran
Malaysia
KSA
UAE
VPN PROTOCOL (S) IN SUMMARY
Which VPN Protocol you ought to utilize is your call. It truly contrasts what is the best answer for you in light of your needs. In the event that all you are contemplating is getting a VOIP calls unblocked in Dubai or to watch American Netflix in KSA, then PPTP may be you’re thing. In the event that you are suspicious about your security and would like to ensure “as others consciously conceivable on the Internet” that you are securing your activity, you might need to consider TOR at a VPN supplier with a NO LOG arrangement. On the off chance that you are in a nation, for example, Iran or China OpenVPN may be your most steady and secure decision to overcome profound investigation. In the event that you are setting up your own VPN server, I trust things are more reasonable at this point. On the off chance that you are searching for a VPN supplier and you have setup your brain on what VPN conventions and elements you need and need to checkout a rundown of suppliers which records specs per supplier.