We will begin with a summary of the real contrasts between the diverse VPN conventions and how they influence you, before looking in more detail at the key ideas included in cryptography, and how the NSA’s attack on encryption gauges influences VPN clients.
The exchange beneath is somewhat specialized, and despite the fact that I have endeavored to make it as agreeable as could be expected under the circumstances, you might like to simply hop to the end of the article for a fast synopsis.
Redesign: I have now composed two buddy piece to this article, titled VPN encryption terms clarified (AES versus RSA versus SHA and so on.) and A Complete Guide to IP Leaks. On the off chance that you are occupied with this subject, make sure to look at them!
OpenVPN
OpenVPN is a genuinely new open source innovation that uses the OpenSSL library and SSLv3/TLSv1 conventions, alongside an amalgam of different advances, to give a solid and dependable VPN arrangement. One of its significant qualities is that it is exceptionally configurable, and despite the fact that it runs best on a UDP port, it can be set to keep running on any port, including TCP port 443. This makes movement on it difficult to distinguish one from the other from activity utilizing standard HTTPS over SSL (as utilized by for instance Gmail), and it is along these lines to a great degree hard to piece.
Another point of preference of OpenVPN is that the OpenSSL library used to give encryption underpins various cryptographic calculations (e.g. AES, Blowfish, 3DES, CAST-128, Camellia and the sky is the limit from there), despite the fact that VPN suppliers encryption solely utilize either AES or Blowfish. 128-piece Blowfish is the default figure incorporated with OpenVPN, and albeit by and large thought to be secure, it has known shortcomings, and even its maker was cited in 2007 as saying ‘right now, however, I’m stunned’s despite everything it being utilized. In the event that individuals ask, I suggest Twofish’.
AES is the more current innovation, has no known shortcomings, and on account of its selection by the US government for use in ensuring encryption “secure” information, is for the most part considered the ‘best quality level’ with regards to encryption. The way that it has a 128-piece square size as opposed to Blowfish’s 64-bit piece estimate likewise implies that it can deal with bigger (more than 1 GB) documents superior to anything Blowfish. Be that as it may, both figures are NIST guaranteed, which while not generally perceived as issue, we have issues with. See beneath for an exchange about this.
How quick OpenVPN performs relies on upon the level of encryption utilized, albeit in fact speaking IPSec is quicker than OpenVPN on the grounds that encryption/decoding is performed in the piece, and in light of the fact that it takes into account multi-threading, which OpenVPN does not.
OpenVPN has turned into the default VPN association sort, keeping in mind locally upheld by no stage, is generally bolstered on most through outsider programming (counting both iOS and Android).
Contrasted with PPTP and L2TP/IPsec, OpenVPN can be a bit fiddly to set up (in spite of the fact that this is an extremely subjective judgment.) When utilizing bland OpenVPN programming as a part of specific, (for example, the standard open source OpenVPN customer for Windows), it is important to download and introduce the customer, as well as to download and setup extra arrangement records. Numerous VPN suppliers get around this setup issue by supplying tweaked VPN customers.
Maybe above all in light of the data acquired from Edward Snowden, it appears that the length of Perfect Forward Secrecy (fleeting key trades, which we talk about later) is utilized, then OpenVPN has not been bargained or debilitated by the NSA. Albeit nobody knows the full capacities of the NSA without a doubt, both the confirmation and the arithmetic emphatically indicate OpenVPN, if utilized as a part of conjunction with a solid figure and transient keys, being the main VPN convention that can be considered really secure. Sadly, not all VPN suppliers use PFS while executing OpenVPN.
Good Things
Exceptionally configurable
Extremely secure (most likely even against the NSA, if Perfect Forward Secrecy is utilized)
Can sidestep firewalls
Can utilize an extensive variety of encryption calculations
Open source (and can along these lines be promptly reviewed for indirect accesses and other NSA style altering)
Bad Things
Needs outsider programming
Can be fiddly to set up
Support on cell phones is enhancing, however is not comparable to on the desktop
PPTP
Point-to-Point Tunneling Protocol was produced by a consortium established by Microsoft for making VPN over dialup systems, and all things considered has long been the standard convention for inner business VPN. It is a VPN convention just, and depends on different validation techniques to give security (with MS-CHAP v2 being the most well-known). Accessible as standard on pretty much every VPN competent stage and gadget, and in this manner being anything but difficult to set up without the need to introduce extra programming, it remains a prevalent decision both for organizations and VPN suppliers. It additionally has the upside of requiring a low computational overhead to actualize (i.e. it’s snappy).
In any case, albeit now typically just discovered utilizing 128-piece encryption keys, various security vulnerabilities have become known, the most genuine of which is the likelihood of unencapsulated MS-CHAP v2 Authentication. Utilizing this endeavor, PPTP has been broken inside of 2 days, and despite the fact that Microsoft has fixed the imperfection (using PEAP verification), it has itself issued a proposal that VPN clients ought to utilize L2TP/IPsec or SSTP.
Realizing that PPTP was unstable in any case, it shocked no one to anyone that the NSA more likely than not unscrambles PPTP encryption correspondences as standard. Maybe all the more stressing is that the NSA has (or is currently) in all likelihood unscrambled the unlimited measures of more seasoned information it has put away, which was encoded back when even security specialists considered PPTP to be secure.
Good Things
Customer implicit to pretty much all stages
Easy to set up
Quick
Bad Things
Not in any manner secure (the powerless MS CHAPv2 validation is still the most widely recognized being used)
Unquestionably traded off by the NSA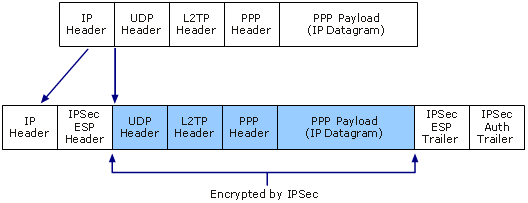
L2TP and L2TP/IPsec
Layer 2 Tunnel Protocol is a VPN convention that all alone does not give any encryption or classification to movement that goes through it. Consequently it is normally actualized with the IPsec encryption suite (like a figure, as talked about underneath) to give security and protection.
L2TP/IPsec is implicit to all cutting edge working frameworks and VPN skilled gadgets, and is generally as simple and fast to set up as PPTP (indeed it more often than not utilizes the same customer). Issues can emerge in any case, in light of the fact that the L2TP convention utilizes UDP port 500, which is all the more effortlessly obstructed by NAT firewalls, and might subsequently require propelled setup (port sending) when utilized behind a firewall (this is dissimilar to SSL which can utilize TCP port 443 to make it unclear from typical HTTPS activity).
IPsec encryption has no major known vulnerabilities, and if legitimately actualized might in any case be secure. In any case, disclosures have emphatically alluded to the standard being bargained by the NSA, and as John Gilmore (security authority and establishing individual from the Electronic Frontier Foundation) clarifies in this post, it is likely that it has been intentionally debilitated amid its configuration stage.
L2TP/IPsec embodies information twice which backs things off, yet this is balanced by the way that encryption/decoding happens in the bit and L2TP/IPsec permits multi-threading (which OpenVPN does not.) The outcome is that L2TP/IPsec is hypothetically quicker than OpenVPN.
Good Things
Normally considered exceptionally secure yet see cons
Simple to set up
Accessible on every single current stage Cons
Speedier than OpenVPN
Bad Things
Might be traded off by the NSA (dubious)
Likely purposely debilitated by the NSA ( dubious)
Can battle with prohibitive firewalls
Related Articles: AES and DES Encryption
SSTP
Secure Socket Tunneling Protocol was presented by Microsoft in Windows Vista SP1, and in spite of the fact that it is currently accessible for Linux, RouterOS and SEIL, it is still to a great extent a Windows-just stage (and there is a snowball’s chance in hellfire of it continually showing up on an Apple gadget!). SSTP utilizes SSL v3, and in this way offers comparable points of interest to OpenVPN, (for example, the capacity to use to TCP port 443 to maintain a strategic distance from NAT firewall issues), and in light of the fact that it is incorporated into Windows might be less demanding to utilize and more steady.
However not at all like OpenVPN, SSTP is a restrictive standard claimed by Microsoft. This implies the code is not open to open examination, and Microsoft’s history of co-working with the NSA, and on-going hypothesis about conceivable indirect accesses worked into the Windows working framework, don’t rouse us with trust in the standard.
Good Things
Extremely secure (relies on upon figure, however more often than not exceptionally solid AES)
Totally coordinated into (Windows Vista SP1, Windows 7, Windows 8)
Microsoft support
Can sidestep generally firewalls
Bad Things
Just truly works in a Windows just environment
Restrictive standard possessed by Microsoft so can’t be autonomously evaluated for indirect accesses and suchlike
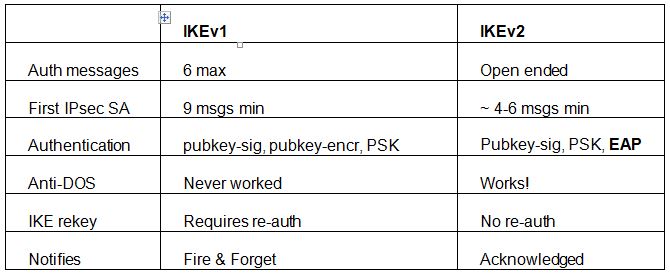
IKEv2
Web Key Exchange (adaptation 2) is an IPSec based burrowing convention that was together created by Microsoft and Cisco, and which is prepared into Windows 7+. Actually talking it (and the more established IKE) is not a VPN convention by any stretch of the imagination, but rather is a control convention for IPSec key trade. It is, be that as it may, frequently regarded as a genuine VPN convention, and it is advantageous (and valuable) to do as such here.
The standard is upheld by Blackberry gadgets, and freely created (and perfect) open source executions are accessible for Linux and other working frameworks. As usual, we are careful about anything created by Microsoft, yet in the event that open source variants are utilized then there ought to be no issue.
Named VPN Connect by Microsoft, IKEv2 is especially great at naturally re-setting up a VPN association when clients incidentally lose their web associations, (for example, when entering or leaving a train burrow).
Portable clients specifically, along these lines, advantage the most from utilizing IKEv2, which due to its backing for the Mobility and Multihoming (MOBIKE) convention, additionally makes it profoundly strong to evolving systems. This is extraordinary news for wireless clients who, for instance, unite their PDAs to a WiFi system while at home however change to portable information use when out on the town, or who frequently switch between hotspots.
IKEv2 is considerably more helpful to Blackberry clients, as it is one of only a handful few VPN conventions bolstered by Blackberry gadgets.
It is not as omnipresent as IPSec (i.e. it is upheld on many less stages), however IKEv2 is considered at any rate on a par with, if not predominant to, L2TP/IPsec as far as security, execution (velocity), and soundness.
It is likewise worth nothing that the more seasoned (and probably less secure) IKE standard (IKE/IPSec) is utilized by pretty much all iOS custom VPN applications, keeping in mind the end goal to make utilization of the official Apple VPN API without jailbreaking the gadget (in spite of the fact that this offers different points of interest, for example, making it simple for suppliers to push redesigned profiles to clients or tie applications to the VPN.)
Good Things
Quicker than PPTP, SSTP and L2TP, as it doesn’t include the overhead connected with Point-to-Point conventions (PPP)
Exceptionally steady – particularly when exchanging organize or reconnecting after a lost web association
Extremely secure encryption – underpins AES 128, AES 192, AES 256 and 3DES figures
Simple to setup (in any event at the client end!)
Convention is upheld on Blackberry gadgets
Bad Things
Not upheld on numerous stages
Actualizing IKEv2 at the server-end is dubious, which is something that could conceivably bring about issues creating
We just trust open source execution.