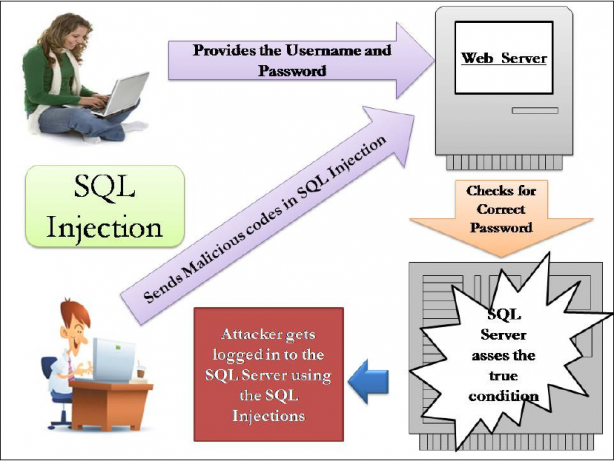
SQL Injection is the hacking system which endeavours to pass SQL charges through a web application for execution by the backend database. If not disinfected appropriately, web applications may bring about SQL Injection assaults that permit programmers to view data from the database and/or even wipe it out
Fundamentally, SQL Injection emerges in light of the fact that the fields accessible for client data permit SQL proclamations to go through and inquiry the database straightforwardly.
Deep into SQL injection:
Web applications permit true blue site guests to submit and recover information to/from a database over the Internet utilizing their favoured web program. Databases are the key to cutting edge sites – they store information required for sites to convey particular substance to guests and render data to clients, suppliers, representatives and a large group of partners. Client certifications, money related and installment data, organization measurements might all be inhabitant inside of a database and got to be honest to goodness clients through off-the-rack and custom web applications. Web applications and databases permit you to consistently maintain your business.
These site components are all helpless to SQL Injection assaults which emerge in light of the fact that the fields accessible for client info permit SQL explanations to go through and inquiry the database specifically.
How can I make sure that I am not in danger zone?
SQL Injection is a standout amongst the most well-known application layer assaults presently being utilized on the Internet. Notwithstanding the way that it is generally simple to ensure against SQL Injection, there are an extensive number of web applications that stay helpless.
As indicated by the Web Application Security Consortium (WASC) 9% of the aggregate hacking episodes reported in the media until 27th July 2006 was because of SQL Injection. Later information from our own examination demonstrates that around 50% of the sites we have examined for the current year are defenceless to SQL Injection vulnerabilities.
It might be hard to answer the inquiry whether your site and web applications are defenceless against SQL Injection particularly on the off chance that you are not a developer or you are not the individual who has coded your web applications.
How to avoid SQL Injection assaults?
Fixing your servers, databases, programming dialects and working frameworks is basic however will not the slightest bit the most ideal approach to counteract SQL Injection Attacks. Firewalls and comparable interruption recognition components give little protection against full-scale web assaults. Since your site needs to be open, security instruments will permit open web movement to correspond with your databases servers through web applications.
What is the effect of SQL Injection?
Once an assailant understands that a framework is defenceless against SQL Injection, he finds himself able to infuse SQL Query/ Commands through a “data” structure field. This is identical to giving the aggressor your database and permitting him to execute any SQL order including DROP to the database.
An assailant may execute discretionary SQL proclamations on the defenceless framework. This may trade off the honesty of your database and/or uncover delicate data. Contingent upon the back-end database being used, SQL infusion vulnerabilities lead to changing levels of information/framework access for the assailant.
Now and again, it might be conceivable to peruse in or work out to documents, or to execute shell charges on the hidden working framework. Certain SQL Servers, for example, Microsoft SQL Server contain put away and amplified methodology. In the event that an assailant can acquire access to these methods, it could spell catastrophe.
Shockingly the effect of SQL Injection is just uncovered when the robbery is found. Information is as a rule unwittingly stolen through different hack assaults constantly. The more master of programmers seldom get got.
At the end:
SQL Injection is one of the numerous web assault systems utilized by programmers to take information from associations. It is maybe a standout amongst the most well-known application layer assault strategies utilized today.
It is the sort of assault that exploits uncalled for coding of your web applications that permits programmer to infuse SQL orders into say a login structure to permit them to get entrance to the information held inside of your database.
It could be argued that data bases are the heart of dynamic sites, and any access to the information is considered a threat to users of the website and those who support it, that’s why SQL injection hacking process comes first on the top 10 traps of security flaws on the site OWASP (Security over the open Internet – specialized in security vulnerabilities for web applications project).