AES (Rijndael)
The calculation Encryption Algorithm was designed by Joan Daemen and Vincent Rijmen. The National Institute of Standards and Technology has as of late chosen Encryption Algorithm as an Advanced Encryption Standard (AES).
The figure has a variable square length and key length. Creators of the Encryption Algorithm at present determine how to utilize keys with a length of 128, 192, or 256 bits to encode hinders with a length of 128 bits.
BestCrypt utilizes Rijndael with a 256-bit enter in LRW and XTS modes.
Blowfish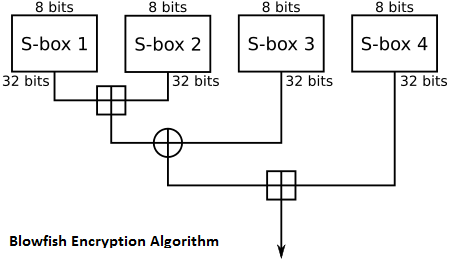
The Blowfish is a quick Encryption Algorithm planned by Bruce Schneier. He is with no doubt understood as the president of Counterpane Systems, a security counseling firm, and the creator of Applied Cryptography: Protocols, Encryption Algorithms, and Source Code.
The Blowfish Encryption Algorithm calculation was uniquely intended to encode information on 32-bit chip. Blowfish is altogether quicker than DES and GOST when executed on 32-bit chip, for example, Power PC or the Pentium.
The first Blowfish paper was introduced at the First Fast Software Encryption Algorithm workshop in Cambridge, UK.
BestCrypt utilizes the Blowfish with 448-bit key length, 16 rounds and 128-bit obstructs in LRW mode.
CAST
CAST-128 Encryption Algorithm is a prevalent 64-bit piece figure permitting key sizes up to 128 bits. The name CAST remains for Carlisle Adams and Stafford Tavares, the designers of CAST.
BestCrypt uses CAST with 128-bit enter in LRW mode.
GOST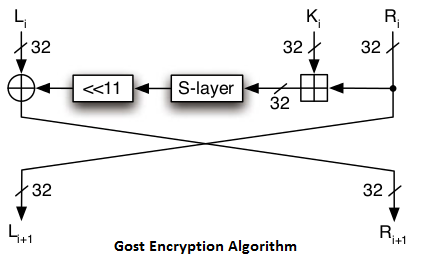
The Government Standard of the USSR 28147-89, Cryptographic assurance for Data Protection Systems, seems to have assumed the part in the previous Soviet Union (not just in Russia) like that played by the US Data Encryption Standard Encryption Algorithm (FIPS 46). At the point when issued, GOST bore the insignificant order ‘For Official Use,’ however is presently said to be generally accessible in programming both in the previous Soviet Union and somewhere else. The prologue to GOST 28147-89 contains a captivating comment that the cryptographic change calculation “does not put any constraints on the mystery level of the secured data.”
The GOST 28147-89 standard Encryption Algorithm incorporates yield input and figure criticism methods of operation, both restricted to 64-bit pieces, and a mode for delivering message confirmation codes.
BestCrypt utilizes GOST 28147-89 with 256-bit enter in LRW mode.
Twofish
Twofish is a symmetric piece figure; a solitary key is utilized for encryption and unscrambling. Twofish has a piece size of 128 bits and acknowledges keys of any length up to 256 bits.
The National Institute of Standards and Technology (NIST) explored Twofish as one of the possibility for the substitution of the DES encryption calculation. As the creators of the calculation state, “we have spent more than one thousand hours cryptanalyzing Twofish, and have discovered no assaults that go anyplace close breaking the full 16-round variant of the figure.”
BestCrypt utilizes an entire 16-round adaptation of Twofish and a greatest conceivable 256-bit encryption key length in LRW and XTS modes.
Data Encryption Standard (DES)
The Data Encryption Standard (DES) is a typical Encryption Algorithm standard for information encryption and a type of private key cryptography (SKC), which utilizes one and only key for encryption and unscrambling. public key cryptography (PKC) utilizes two keys, i.e., one for encryption and one for unscrambling.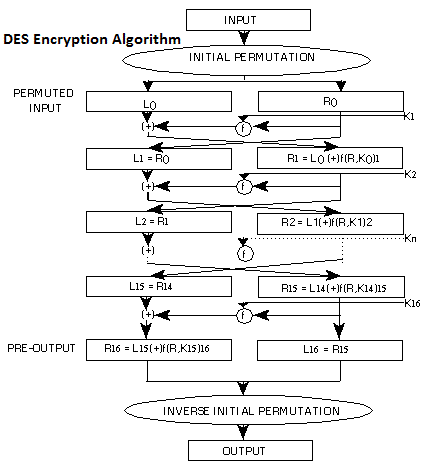
In 1972, the National Bureau of Standards (NBS) drew nearer the Institute for Computer Sciences and Technology (ICST) to devise an encryption algorithm to secure put away and transmitted information. The encryption algorithm would be openly accessible, however its key would be best to be private.
The National Security Agency (NSA) helped with the cryptographic algorithm assessment forms, and one year later, accommodation welcomes were posted in the Federal Register. In any case, the entries were inadmissible. A year after, a second welcome was posted, which brought about an accommodation from IBM. In 1975, specialized details were distributed for remarks in the Federal Register, and examination and audit started. In 1977, NBS issued the calculation, i.e., DES, as Federal Information Processing Standards (FIPS) 46.
In the blink of an eye from there on, the U.S. Bureau of Defense (DoD) executed DES. Particulars are delineated in FIPS production 46-3, FIPS 81, ANSI X3.92 and ANSI X3.106. For security reasons, the U.S. government has never approved fares of this encryption programming.
There are no less than 72 quadrillion DES key potential outcomes. In 1993, NIST recertified DES, and the Advanced Encryption Standard (AES) turned into its informal substitution.
Know more about encryption from here



